tcpdump is a common packet analyzer that runs under the command line. It allows the user to intercept and display TCP/IP and other packets being transmitted or received over a network to which the computer is attached. Distributed under the BSD license,[3] tcpdump is free software.
Tcpdump works on most Unix-like operating systems: Linux, Solaris, BSD, Mac OS X, HP-UX and AIX among others. In those systems, tcpdump uses the libpcap library to capture packets. The port of tcpdump for Windows is called WinDump; it uses WinPcap, the Windows port of libpcap.
How to Install tcpdump in Linux
Install tcpdump on Debian, Ubuntu, Mint linux using command:
# sudo apt-get install tcpdump -y
Install tcpdump on Fedora, CentOS and RHEL linux following command:
# yum install tcpdump
Once tcpdump tool is installed on systems, you can continue to browse following commands with their examples.
Capture Packets from Specific Interface
When you execute tcpdump command without any option, it will capture all the packets flowing through all the interfaces. -i option with tcpdump command, allows you to filter on a particular ethernet interface.
# tcpdump -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:37:14.550522 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1578168831:1578169023, ack 3730519324, win 771, options [nop,nop,TS val 2916891 ecr 2882812], length 192 08:37:14.550713 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 541, options [nop,nop,TS val 2882823 ecr 2916891], length 0 08:37:14.551493 IP 192.168.1.80.48393 > resolver1.opendns.com.domain: 23054+ PTR? 88.1.168.192.in-addr.arpa. (43) 08:37:14.597605 IP resolver1.opendns.com.domain > 192.168.1.80.48393: 23054* 0/1/0 (102) 08:37:14.598305 IP 192.168.1.80.37674 > resolver1.opendns.com.domain: 36143+ PTR? 80.1.168.192.in-addr.arpa. (43) 08:37:14.649412 IP resolver1.opendns.com.domain > 192.168.1.80.37674: 36143* 0/1/0 (102) ...
Capture Only N Number of Packets
When you execute tcpdump command it gives packets until you cancel the tcpdump command. Using -c option you can specify the number of packets to capture.
# tcpdump -c 2 -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:38:57.023840 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1578778495:1578778687, ack 3730520300, win 771, options [nop,nop,TS val 3019365 ecr 2908433], length 192 08:38:57.024187 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 1233, options [nop,nop,TS val 2908441 ecr 3019365], length 0 2 packets captured 6 packets received by filter 0 packets dropped by kernel
Print Captured Packets in ASCII
The following tcpdump syntax prints the packet in ASCII.
# tcpdump -A -i eth0 -c 2 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:41:42.839829 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1580671503:1580671695, ack 3730522172, win 771, options [nop,nop,TS val 3185181 ecr 2949887], length 192 E.....@.@......P...X...2^7"..[@<........... .0...-..Jr..x...p&y8*c....0i.....o...;h.I.0.R].Ll....R@;.z..}... .Dk....A...*....>....By..>........M...m..y....u..u;i..T.,P.........;u`....i.?......q.VF.'.U 08:41:42.840144 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 1792, options [nop,nop,TS val 2949895 ecr 3185181], length 0 E..4..@.@..#...X...P.2...[@<^7"......[..... .-...0.. 2 packets captured 6 packets received by filter 0 packets dropped by kernel
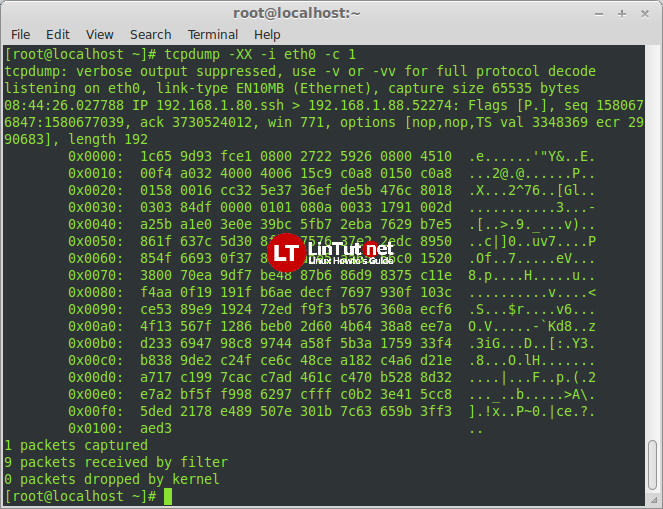
Display Captured Packets in HEX and ASCII using tcpdump -XX
Some users might want to analyse the packets in hex values. tcpdump provides a way to print packets in both ASCII and HEX format.
# tcpdump -XX -i eth0 -c 2
Display Available Interfaces
To list number of available interfaces on the system, run the following command with -D option.
# tcpdump -D 1.eth0 2.usbmon1 (USB bus number 1) 3.usbmon2 (USB bus number 2) 4.any (Pseudo-device that captures on all interfaces) 5.lo
Capture the packets and write into a file using tcpdump -w
tcpdump allows you to save the packets to a file, and later you can use the packet file for further analysis.
# tcpdump -w file.pcap -i eth0 tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 10 packets captured 10 packets received by filter 0 packets dropped by kernel
Reading the packets from a saved file using tcpdump -r
You can read the captured pcap file and view the packets for analysis, as shown below.
[ads]
# tcpdump -r file.pcap reading from file file.pcap, link-type EN10MB (Ethernet) 08:48:42.977710 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1580681775:1580681903, ack 3730526668, win 771, options [nop,nop,TS val 3605318 ecr 3054921], length 128 08:48:42.978087 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 128, win 1792, options [nop,nop,TS val 3054930 ecr 3605318], length 0 08:48:48.189810 IP 192.168.1.253.nfs > 239.255.255.250.ssdp: UDP, length 330 08:48:49.939291 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [P.], seq 1:49, ack 128, win 1792, options [nop,nop,TS val 3056670 ecr 3605318], length 48
Capture IP address Packets
In all the above examples, it prints packets with the DNS address, but not the ip address. The following example captures the packets and it will display the IP address of the machines involved.
# tcpdump -n -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:52:03.880624 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1581156671:1581156863, ack 3730531052, win 771, options [nop,nop,TS val 3806222 ecr 3105148], length 192 08:52:03.881068 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 192, win 3308, options [nop,nop,TS val 3105155 ecr 3806222], length 0 08:52:03.881825 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 192:560, ack 1, win 771, options [nop,nop,TS val 3806223 ecr 3105155], length 368 08:52:03.882112 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 560, win 3331, options [nop,nop,TS val 3105156 ecr 3806223], length 0
Capture only TCP Packets.
To capture packets based on TCP port, run the following command with option tcp.
# tcpdump -i eth0 tcp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:53:59.609774 IP 192.168.1.80.ssh > 192.168.1.88.52274: Flags [P.], seq 1581594191:1581594383, ack 3730533372, win 771, options [nop,nop,TS val 3921951 ecr 3134081], length 192 1 packets captured 5 packets received by filter 0 packets dropped by kernel
Capture Packet from Specific Port
Let’s say you want to capture packets for specific port 22, execute the below command by specifying port number 22 as shown below.
# tcpdump -i eth0 port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:55:31.321096 IP 192.168.1.88.44209 > 192.168.1.80.http: Flags [S], seq 3335310211, win 14600, options [mss 1460,sackOK,TS val 3157015 ecr 0,nop,wscale 7], length 0 08:55:31.321737 IP 192.168.1.88.44210 > 192.168.1.80.http: Flags [S], seq 185161599, win 14600, options [mss 1460,sackOK,TS val 3157016 ecr 0,nop,wscale 7], length 0 08:55:31.378373 IP 192.168.1.88.44211 > 192.168.1.80.http: Flags [S], seq 2915876395, win 14600, options [mss 1460,sackOK,TS val 3157030 ecr 0,nop,wscale 7], length 0 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel
Capture Packets from source IP
To capture packets from source IP, say you want to capture packets for 192.168.0.2, use the command as follows.
# tcpdump -i eth0 src 192.168.1.88 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:57:23.275553 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 1582390207, win 6516, options [nop,nop,TS val 3185004 ecr 4125616], length 0 08:57:23.365741 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 193, win 6516, options [nop,nop,TS val 3185026 ecr 4125706], length 0 08:57:23.367421 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 385, win 6516, options [nop,nop,TS val 3185027 ecr 4125708], length 0 08:57:23.368405 IP 192.168.1.88.52274 > 192.168.1.80.ssh: Flags [.], ack 577, win 6516, options [nop,nop,TS val 3185027 ecr 4125709], length 0 ... 223 packets captured 223 packets received by filter 0 packets dropped by kernel
Capture Packets from destination IP
To capture packets from destination IP, say you want to capture packets for 50.116.66.139, use the command as follows.
# tcpdump -i eth0 dst 192.168.1.1 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 08:58:57.790236 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 1, length 64 08:58:58.791754 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 2, length 64 08:58:59.793019 IP 192.168.1.80 > 192.168.1.1: ICMP echo request, id 54280, seq 3, length 64 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel