If you run a Linux server, and you’re on top of things, you’ve heard of GHOST.. which is a heap buffer overflow vulnerability announced today. Distributions are working on a patch and some are ready now.
About GHOST Vulnerabilities
The GHOST vulnerability is a serious weakness in the Linux glibc library. It allows attackers to remotely take complete control of the victim system without having any prior knowledge of system credentials. CVE-2015-0235 has been assigned to this issue.
More about GHOST Vulnerabilities
How to Patch Ghost On CentOS/RHEL
There is a patch available for CentOS 5, CentOS 6, CloudLinux5 and CloudLinux 6 in the repos.. soon for Debian as well. Here is how to patch in CentOS (or other yum / rhel flavor)
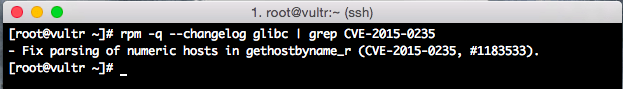
First, let’s see if you’re patched already by typing:
# rpm -q --changelog glibc|grep CVE-2015-0235
If you’re patched already, you’ll see:
- Fix parsing of numeric hosts in gethostbyname_r (CVE-2015-0235, #1183532).
Example:
[ads]
IF you do not see that, check to if the update is in your repos yet:
# yum clean all && yum update glibc
If it says “No Packages marked for Update” then try again later…
If it shows you an update is available, run the update, then reboot (because there are a lot of various services that use glibc and restarting is a lot easier than finding and restarting each one).
# shutdown -r now
How to Patch Ghost On Ubuntu/Debian
For currently supported versions of Ubuntu or Debian, update all of your packages to the latest version available via apt-get dist-upgrade:
$ sudo apt-get update && sudo apt-get dist-upgrade
Then respond to the confirmation prompt with y.
When the update is complete, reboot the server with this command:
$ sudo reboot
A reboot is necessary since the GNU C Library is used by many applications that must be restarted to use the updated library.
How can Ubuntu 11.04 be patched?