Linux Malware Detect (LMD) or simply Maldet is a free malware scanner designed for Linux machines released under the GNU GPLv2. It is specially designed around the threats in the shared hosted environment. LMD uses threat data from network edge intrusion detection systems to get the actual malware that is used in attacks and generates a variety of signatures for detection.
In addition to these features, LMD threat data can also be extracted from user submissions with the checkout feature in LMD from malware resources. It uses signatures such as HEX pattern and MD5 file hashes. They can also be extracted from a variety of detection tools including ClamAV.
In this article we will explain how to install and configure Linux Malware Detect along with ClamAV in RHEL 7.0/CentOS 7.0.
Install LMD on CentOS 7 / RHEL 7
LMD is not available on CentOS official repositories as a pre-built package, but it is available as a tarball from the LMD project web site. Download the latest version of LMD using the following command.
# cd /tmp/ # curl -O http://www.rfxn.com/downloads/maldetect-current.tar.gz
Open the already downloaded Linux Malware file:
# tar -zxvf maldetect-current.tar.gz # cd maldetect*
Run the installation script install.sh present in the extracted directory.
# bash install.sh
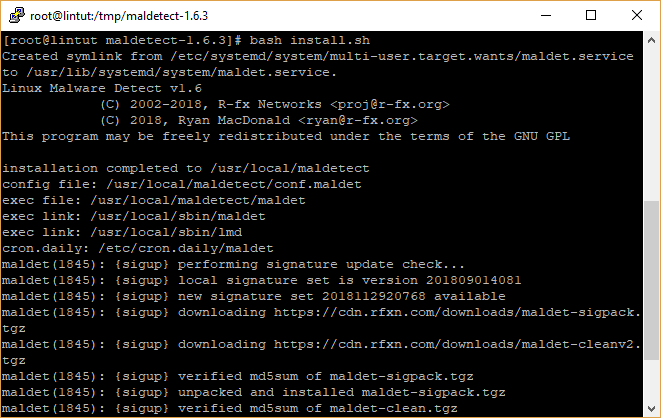
Configure Linux Malware Detect
Linux Malware Detect configuration file is /usr/local/maldetect/conf.maldet and it can be modified as per the requirements below:
# vi /usr/local/maldetect/conf.maldet
Below are some of the important settings you should have it on your system for successful detection and deletion of threats.
[ads]
# Enable Email Alerting email_alert="1" # Email Address in which you want to receive scan reports email_addr="lintut@gmail.com" # Use with ClamAV scan_clamscan="1" # Enable scanning for root owned files. Set 1 to disable. scan_ignore_root="0" # Move threats to quarantine quarantine_hits="1" # Clean string based malware injections quarantine_clean="1" # Suspend user if malware found. quarantine_suspend_user="1" # Minimum userid value that be suspended quarantine_suspend_user_minuid="500"
Installing ClamAV on RHEL/CentOS 7.0
LMD performs better in scanning large file sets with ClamAV. ClamAV (Clam Antivirus) is an open source antivirus solution to detect virus, malware, trojans and other malicious programs.
ClamAV is available on EPEL repository, so configure it on your CentOS / RHEL machine.
# rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
Install ClamAV using YUM command.
# yum -y install clamav clamav-devel clamav-update inotify-tools
Now, update the ClamAV virus databases using the following command.
# freshclam
No additional configuration is required with LMD as the use of ClamAV with LMD is enabled by default.
[box type=”note” align=”” class=”” width=””]Note: That these are only the basic instructions to install ClamAV in order to integrate it with LMD. We will not go into detail as far as ClamAV settings are concerned since as we said earlier, LMD signatures are still the basis for detecting and cleaning threats.[/box]
Testing Linux Malware Detect
Now it’s time to test our recent LMD / ClamAV installation. Instead of using real malware, we will use the EICAR test files, which are available for download from the EICAR web site.
# cd /tmp/ # wget http://www.eicar.org/download/eicar_com.zip # wget http://www.eicar.org/download/eicarcom2.zip
Now, scan the directory for malware:
# maldet --scan-all /tmp
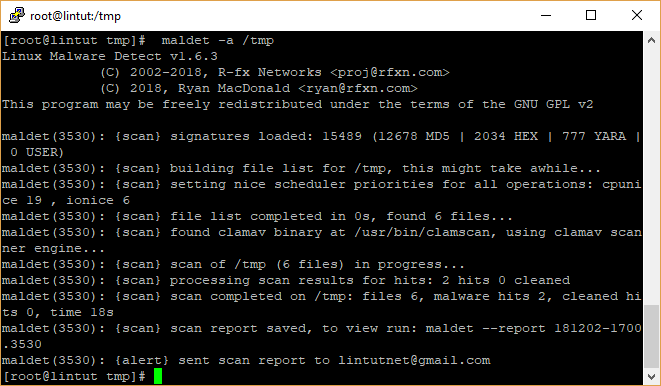
From the output, you can see that LMD is using ClamAV scanner engine to perform the scan and resulted in finding two malware hits.
Linux Malware Detector Scan Report
LMD stores scan reports under /usr/local/maldetect/sess/. Use the maldet command with SCAN ID to see the detailed scanning report.
maldet --report 181202-1700.3530
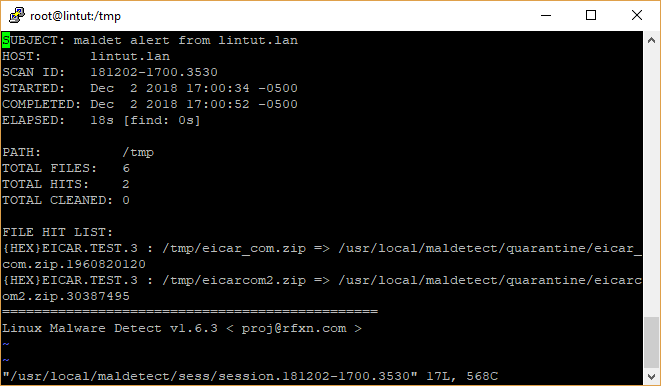
You can see that both files are now quarantined.
Update Linux Malware Detect
Use the following command to update your LMD.
# maldet -d
To update LMD signatures, run:
# maldet -u
Conclusion
Congratulations, LMD is now installed in CentOS 7 system and ready for use. Follow these steps and make the necessary edits to configure LMD to your needs.
Great article!!
Can you help solving following issue:
————-
Failed to watch /usr/local/; upper limit on inotify watches reached!
Please increase the amount of inotify watches allowed per user via `/proc/sys/fs/inotify/max_user_watches’.
————-
how safe is to increase max_user_watches value? in /proc/sys/fs/inotify/max_user_watches??
Thanks,
When I scan eicar test files using clamscan command it finds viruses but when I use lmd –scan-all it doesn’t find anything!! I tried clamav_scan=0 and 1 in conf.maldet.
@Robert, make the following change – this worked for me because the files were root owned and were being skipped. ( https://forum.vestacp.com/viewtopic.php?t=17511 )
# Enable scanning for root owned files. Set 1 to disable.
scan_ignore_root=”0″