Fail2ban, it is a security based application for your Unix based server. The fail2ban service is commonly used to protect your SSH and FTP from unauthorized connection. Fail2ban is a daemon that uses python scripts to parse log files for system intrusion attempts and adds custom iptables rules defined by you in the configuration file to ban access to certain ip addresses.
This guide explains how to install Fail2ban software on RHEL/CentOS 7.
Installing Fail2Ban on RHEL, CentOS 7
To install Fail2Ban on RHEL and CentOS 7, run the commands below to enable EPEL 7 repository.
wget dl.fedoraproject.org/pub/epel/7/x86_64/e/epel-release-7-1.noarch.rpm rpm -ivh epel-release-7-1.noarch.rpm
Next, run the commands below to install Fail2Ban
yum install fail2ban -y
Confiure Fail2Ban
So now fail2ban is installed on your CentOS 7, what next to do is setting up some basic Fail2ban configuration. Here I’ll show you a very basic setup. Now firstly copy default configuration file:
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
[ads]
Now edit jail.local file you copied. Use your favorite text editor like Nano or vi.
nano /etc/fail2ban/jail.local
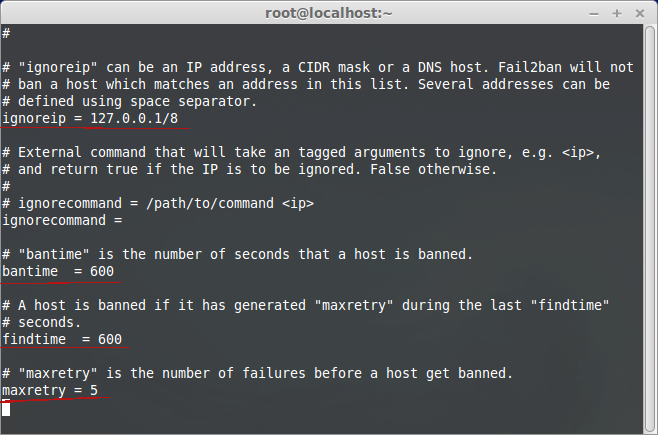
Scroll down the page for all available configuration. There are few lines act as basic setup you can edit as necessary to suit your need including: ignoreip, bantime, findtime, and maxretry. You can read what each line means in the explanation available there.
Write your personal IP address into the ignoreip line. You can separate each address with a space. IgnoreIP allows you white list certain IP addresses and make sure that they are not locked out from your VPS. Including your address will guarantee that you do not accidentally ban yourself from your own virtual private server.
The next step is to decide on a bantime, the number of seconds that a host would be blocked from the server if they are found to be in violation of any of the rules. This is especially useful in the case of bots, that once banned, will simply move on to the next target.
Maxretry is the amount of incorrect login attempts that a host may have before they get banned for the length of the ban time.
Findtime refers to the amount of time that a host has to log in. T
Now restart Fail2ban so the new configuration can take effect.
systemctl restart fail2ban.service
That’s it.
what if you are using firewalld in CentOS 7 instead of iptables?
There’s a fail2ban-firewalld.noarch package in epel (at least in release 7-2) – it gets installed as a dependency when installing fail2ban.
@rasho: There’s an easier way for installing epel itself (at least for CentOS):
yum install epel-release.noarch
I have installed this on to servers and it still will not ban anyone. I disabled firewalld and am running iptables. Does that matter? I get this kind of response from logwatch nightly…
sshd:
Authentication Failures:
root (103.41.124.21): 4842 Time(s)
root (103.41.124.59): 4785 Time(s)
root (62-210-172-56.rev.poneytelecom.eu): 3609 Time(s)
root (222.73.7.32): 1275 Time(s)
root (62-210-172-181.rev.poneytelecom.eu): 1143 Time(s)
root (62-210-141-172.rev.poneytelecom.eu): 1113 Time(s)
root (1.93.29.136): 805 Time(s)
root (123.125.219.130): 391 Time(s)
root (61.174.51.228): 348 Time(s)
root (122.225.109.115): 286 Time(s)
And I know fail2ban is running because I get this with ps -ax | grep fail2ban
3242 ? S 0:00 /usr/bin/python /usr/bin/fail2ban-server -b -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid -x
What can I check to see why it isn’t working?
nic ciekawego
If you don’t enable any jails, fail2ban won’t do anything. All jails are disabled by default.