This guide will shown you how to boot an ISO image file that stored in your hard drive. Booting an ISO on your hard drive is useful for testing new versions of Linux ISO file without using up a CD/DVD or USB Stick. On this case I will boot Ubuntu 13.04 iso directly from hard disk via the Grub2 boot menu. Create a directory named iso in your root folder using this command:
# sudo mkdir /isoimage
Now copy ubuntu 13.04 iso file (ubuntu-13.04-desktop-i386.iso) to directory /isoimage :
# sudo cp -v ~/ISOFILE/ubuntu-13.04-desktop-i386.iso /isoimage
Edit /boot/grub/grub.cfg file with following command:
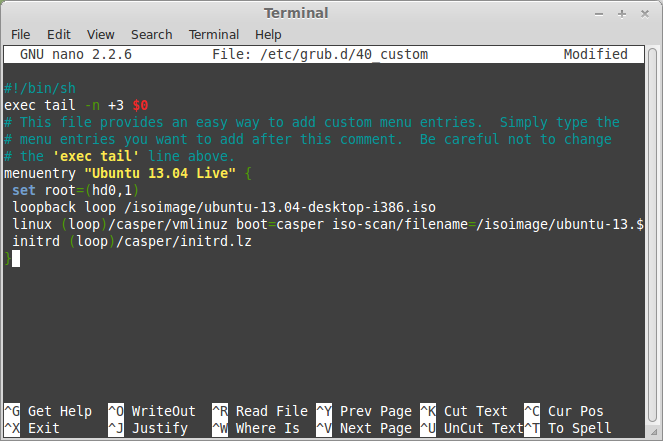
# sudo nano /etc/grub.d/40_custom
add these lines to Custom GRUB Configuration file (/etc/grub.d/40_custom):
menuentry "Ubuntu 13.04 Live" {
set root=(hd0,1)
loopback loop /isoimage/ubuntu-13.04-desktop-i386.iso
linux (loop)/casper/vmlinuz boot=casper iso-scan/filename=/isoimage/ubuntu-13.04-desktop-i386.iso noprompt noeject
initrd (loop)/casper/initrd.lz
}
After this enter command:
# sudo update-grub
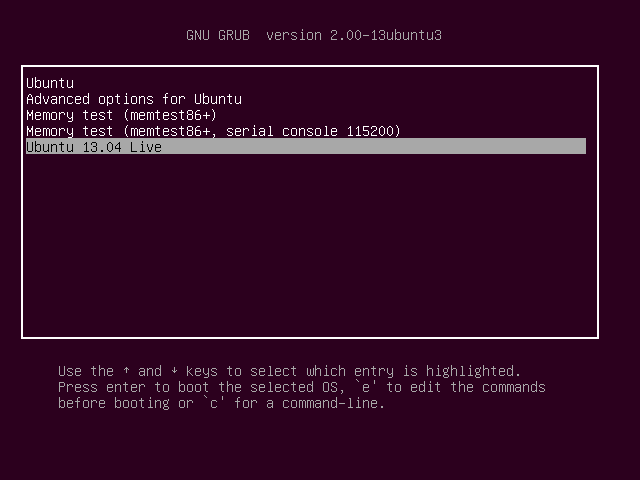
Save your file and exit. Then reboot ubuntu and hold down the Shift key to bring up the Grub boot menu. Select Ubuntu 13.04 Live to boot ubuntu 13.04 iso image from hard drive
Reference: Grub examples
How about Windows iso?
Don’t know about MS Windows ISO but you can boot VHD files with Windows 7 Enterprise/Ultimate and with Windows 8 Enterprise/Professional without any problem. The better is to install Windows Server 2012 (An soon 2012 R2) as a Native system then make the VHD you want by creating virtual computers in HyperV (Any MS OS will work as a charm) Sysprep you installation and modify your Bootmanager configuration with BCEDIT… 😉
You forgot update-grub
Thank you Mister. I am added this in post.
Let me make sure yet, but if there is a security flaw here. Some crafty user can change entries in the grub as it has escalated privileges via sudo. In this way it can run the system in which you have the right root. It can, for example, run the Linux Kali. After reboot, can do whatever he wants with the machine. Am I right?
No you’re not right. Before you get too excited, That “crafty” user would have to have been setup in /etc/sudoers first which kinda suggests they would be a “trusted” user on the system already. Also you don’t need to reboot, sudo -s will “pop” you a root shell right there.
Look Ma, I’m owning my system…. oh no that’s just how it’s suppose to function.
or sudo su –
or sudu su – username
for a proper login like environment rather than the sudoish proxy env